If your life depended on the security and privacy of your
Internet connection, would you trust what you are using now? Or would you prefer
the same security the US Army uses for all communication classified as
TOP SECRET?
Did you know that almost all the data you send and receive over the Internet
is transmitted unencrypted and can be easily stolen? Spammers, hackers, data
thieves,
identity thieves and just about all kinds of bad guys simply love it. And yes,
this list may just as well include even your own government, your Internet
Service Provider or an overly curious boss or spouse. If you are not protecting yourselves, you
are an easy prey for them!
But what if there was a solution to this problem?
A sophisticated, yet
easy to use system that would protect the sensitive data you send and receive over the
Internet using an encryption technique so powerful that even the US
Department of Defense and the US Army is using it for protecting information
classified TOP SECRET? Encryption technique so powerful you
would need at least a few hundred years to break even with huge computer
networks? Encryption technique so powerful that even the best funded
intelligence agencies cannot break it?
Congratulations: You've just found such a solution. Welcome to
IdentityCloaker.com!
We will protect you from Internet spies and prying eyes!
The technology used to cause you harm is becoming more and
more affordable and widespread among the bad guys. What was restricted to
intelligence agencies and law enforcement just a few years ago, is now available
on the open market. The danger is *very* real and far more serious than you may
think. Obviously, we cannot protect you from every possible threat on the Internet.
But we will do our best to help you survive the Wild Wild West. And we will do
more than that!
What is Identity Cloaker?
In short, Identity Cloaker could be defined as an "Internet Privacy Protection
Service". Its main goal is to protect your privacy by encrypting the data
sent over the Internet in the most vulnerable part of the data transmission path,
and by hiding your physical location and IP address from prying eyes. There are, however, more advantages...
Do you want to see a website that is normally blocked by your Internet
Service Provider (ISP) or network administrator, or that can not be viewed
from your country? Do you manage Internet marketing campaigns targeted to
specific geographical locations through IP address based content delivery
and want to see the advertisements exactly as your potential customers in
different countries see them? Identity Cloaker can help you with that too.
What is Identity Cloaker *NOT* ?
1. Identity Cloaker is not a "Free Proxy Server Service".
Identity Cloaker is not some rubbish free proxy service that
hands you a huge list of so called free proxy servers, that are
either overloaded, not working, or even infected by viruses and other
nasty stuff. We do not rely on rubbish and neither should you! Instead,
IdentityCloaker.com operates its own growing network of private servers
around the world.
It's also important to note that free proxy servers are not
usually free at all. In most situations the administrators of the
physical server computers do not even know they are running a proxy
server. They simply either misconfigured some proxy server software they
intended to install for their own needs, or their server had been
compromised by a hacker who then installed such proxy server software
and probably caused some more evil along the way.
There are also reports of some free proxy servers being directly
owned by the bad guys. They may be owned by hackers operating on their
own, and sometimes even in organized gangs. They use such free proxy
servers as a lure that helps them in phishing attacks, gather your web
surfing habits, steal your sensitive information sent through such
servers etc. The risk is too high!
2. Identity Cloaker is not a "Web Based Proxy Service".
Web based proxy services (those websites you visit and enter the URL
address you want to access into a form field provided on such a
website), are usually Perl or PHP scripts that hide your IP address. To
use them, you must change your surfing habits and they do not work in
every situation because they have to rewrite the source html code - for
example to change image paths. This very often results in problems.
Not every page is displayed, or is displayed incorrectly. SSL
protected websites (those whose address in the URL bar starts with https://) and websites needing authentication,
such as membership websites,
work rarely. Web proxies can easily be blocked by network
administrators. And even if their domain is not blocked (yet), the
transferred data is unencrypted and it's easy for the network admin to
recognize what you do with such a service.
Imagine a situation when you want to visit a website that's normally
blocked. You use web proxy and visit the blocked web through it.
However, the network administrator (or your Internet Service Provider,
boss, spouse or hacker...) can see you visited the
web proxy website - but they can also see what you were doing when using
it! They can find out the visited websites and see the transferred data.
The consequences could be dire. Web based proxy services offer a very
low level of safety. They hide your IP address and allow you to access
*some* websites you normally could not. But that's about it.
3. Identity Cloaker is not "volunteer dependent".
Some anonymity networks and privacy protection services, including
the popular
TOR, rely on volunteers which results in unpredictable quality of
service, usually resulting in very low data transfer speeds and temporal
malfunction. Although such services can very often offer a great level
of security, they are intended mostly for transferring relatively small
amount of data.
By design, such services are generally unsuitable for everyday use
and for any services with high bandwidth requirements such as streaming
radio or video etc. They are also mostly intended for power-users only,
their complexity makes it difficult to use for the average computer
user.
How does Identity Cloaker work?
You simply download a small PC software application (no
installation necessary), run it, and choose one of our private proxy servers which you would
like to be connected through - or simply hit the Connect button if you
want to have one selected automatically.
When you click the Connect
button, a secure data tunnel encrypted with a military class encryption
cipher will be created to the selected proxy server.
This technique is commonly called SSH tunneling.
If you use any standard web browser, such as Internet Explorer,
Microsoft Edge, Google Chrome, Firefox or Safari (on Mac OS), there is nothing more you have to do, it will be
automatically set to use the new secure tunnel for all of your web browsing.
If you use a less common web browser, it's still possible to instruct the
Identity Cloaker application to cloak it too. It's now also possible to
cloak most other applications too.
Enough talking, let's take a look at the most common situations in
pictures:
Situation 1 - Browsing the web without Identity
Cloaker:
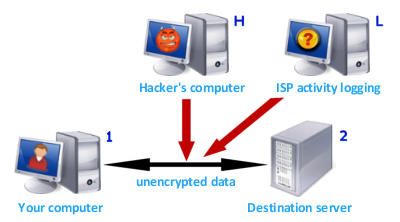
You visit a website - let's call it something.com
from your computer, your computer sends a request to something.com
and retrieves the data sent back from it. This is actually an oversimplification
but generally, it's how it works. The data on the whole path of the
communication between you and something.com is normally unencrypted
(unless secure https/ssl connection is used). Something.com can easily discover your physical location
by reading your IP address. And the part of the communication
between you and your Internet Service Provider is vulnerable to data eavesdropping.
Situation 2 - Browsing the web with Identity
Cloaker:
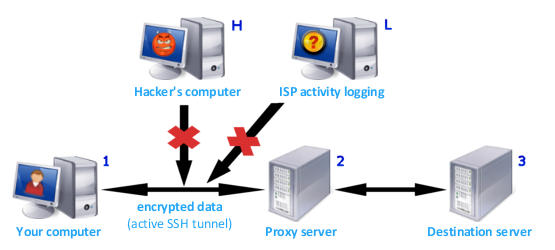
You visit a website - again, let's call it
something.com. The request is sent through the established encrypted
secure tunnel to the chosen Identity Cloaker proxy server. This is done in
the background - you do not even have to know about it. The proxy server
then sends the request to something.com on your behalf, receives
the answer and forwards it back to you - again through the encrypted secure
tunnel. At all time, something.com was communicating with the proxy
server and does not even know about you! The proxy server works as the
middleman.
For more examples, please take a look at our illustrations at the
How it works page.
How large is the IdenityCloaker.com network of secured proxy servers?
Our network of secured private proxy servers is growing all the time.
Currently, we have our servers located in Germany, Netherlands,
France, United
Kingdom, Italy, Ireland, Sweden, Canada, USA, Poland, Russia, Switzerland, Australia, Spain,
Norway, Portugal, Austria, Hong Kong, Singapore and Czech Republic. If there is interest, we may also add servers
in other
countries and parts of the world too.
Our system is very flexible and has been designed to be
able to increase its capacity easily, without sacrificing quality of the
service offered to our valued customers.
Right now, there are 34 servers with 550 IPs in
18 countries in the Identity Cloaker network
We should mention one thing. When we talk about "proxy servers" we mean
our own secured private proxy servers. Those are either physical computers
or Virtual Dedicated Servers we have
rented in several data centers throughout the world. We pay a monthly fee
for all of them. They all have 100Mbit or 1Gbit ports with monthly traffic allowance
usually in the terabytes.
If you have no idea what that means, it means that we have enough
capacity to offer any customer more than reasonable broadband speed of
data transfer. We do not rely on some low quality free proxy servers that
are almost always oversaturated, overloaded, and may be even infected by
malevolent software threatening - not helping, your privacy!
Another important characteristic of the IdentityCloaker.com system is
that the data transmitted between you and our private proxy servers is
encrypted using a military class encryption technique! This is an extremely important
feature, not offered even by premium services offering access to
private proxy servers.
What is necessary to be able to use Identity Cloaker?
As long as you can view this page and are using a Microsoft Windows
XP, Windows Vista, Windows 7, Windows 8 or Windows 10 computer or run MS Windows XP, Vista or
7 or 8 or 10 in a virtualized
environment, or you have any modern Mac computer you should be able to use Identity Cloaker. There are no
special requirements, really.
You can now also connect to our VPN (Virtual Private Network) servers
using any Android smartphone or tablet, iPhone or iPad.
Identity Cloaker will work even if you have to access the Internet
through an "internal" or company proxy server which is a common situation in some
companies and institutions. However, if Identity Cloaker does not work for you for any
reason and our technical support is not able to help you solve the
problem, we will refund your order without delay. Please see the "Fair
Deal Guarantee" info box below. There is absolutely no risk for
you!
By the way, there is one thing we should mention but it's somewhat
controversial... Identity Cloaker does use an extremely powerful
technique that allows you to override any web browsing restrictions set
on the company firewall level by its administrator. This technique is
sometimes colloquially called "punching holes in firewalls".
Identity Cloaker creates a secure tunnel connection between your PC
(or another device, see above) and one of the Identity Cloaker proxy servers. Once it is established
(through the company firewall), you gain the same web access rights as
the Identity Cloaker proxy server itself. And since the proxy server can
access just about any website, so can you...and without anyone knowing!
For more details about how this all works, please take a look at the
How it works page.
Identity Cloaker is a very powerful tool, please use it responsibly
and with caution!
It all sounds a bit complicated, how easy is it to use?
Identity Cloaker is a complex and sophisticated system, no doubt about it. However,
from the very beginning, it has been designed to be very easy to use
even for
the average computer user. You do not really need to care about what's
going on in the background, you do not need to worry about the technical
stuff at all.
All you need to do is to download a small Windows PC
or Mac application (Android and iOS solutions are available too), follow a few easy to understand on-screen instructions
(normally just hitting the Enter button a few times) to "install" it and click the
"Connect" button. How easy is that ;)
Of course, if you do want to know what is going on in the background, or
you just love the technical stuff, we have no problem with that either. Just
take a look at the
How it works page, the Frequently Asked Questions,
or contact us through our helpdesk. We will be more
than happy to answer any question you may have.
UPDATE: Mostly intended for the demanding power users,
we now offer also
OpenVPN
and "L2TP over IPSec"
access to all of our servers beside of our standard service! The
VPN access is currently being offered as a part of the standard
subscription service, with no additional fee.
How much is your privacy worth?
We believe that privacy and safety should not be luxury. While it would
be great if we could offer our services for free, this is,
unfortunately, not possible. And in fact, this is the good news for you! By
charging a small fee we are able to deliver a high quality service, and we can keep improving it. Identity Cloaker is a premium
service, but don't worry, our prices are not premium :)
So how much does it cost to get access to our broadband secured private proxy
servers, super safe surfing through SSH tunneling and VPN backed by 256-bit military
class encryption, our own custom-coded Microsoft Windows XP/Vista/7/8/10/Mac compatible
client software and our exclusive private membership website?
Less than €6.67 a month! Yes, that's six Euros and
sixty seven Cents - you can use our
currency conversion tool to see the amount in your local currency.
So again, what are the main benefits of Identity Cloaker?
But what's most important:
We will protect your privacy!








